This is the third in a multipart series that explores machine learning (ML) within cybersecurity. The first post in this series provided…
Today, I will discuss the threat intelligence process at a fictional but typical financial organization called DPS. The threat intelligence…
Ty Detmer was a better quarterback than Tom Brady because of his superior passing skills. Detmer won the Heisman Trophy…
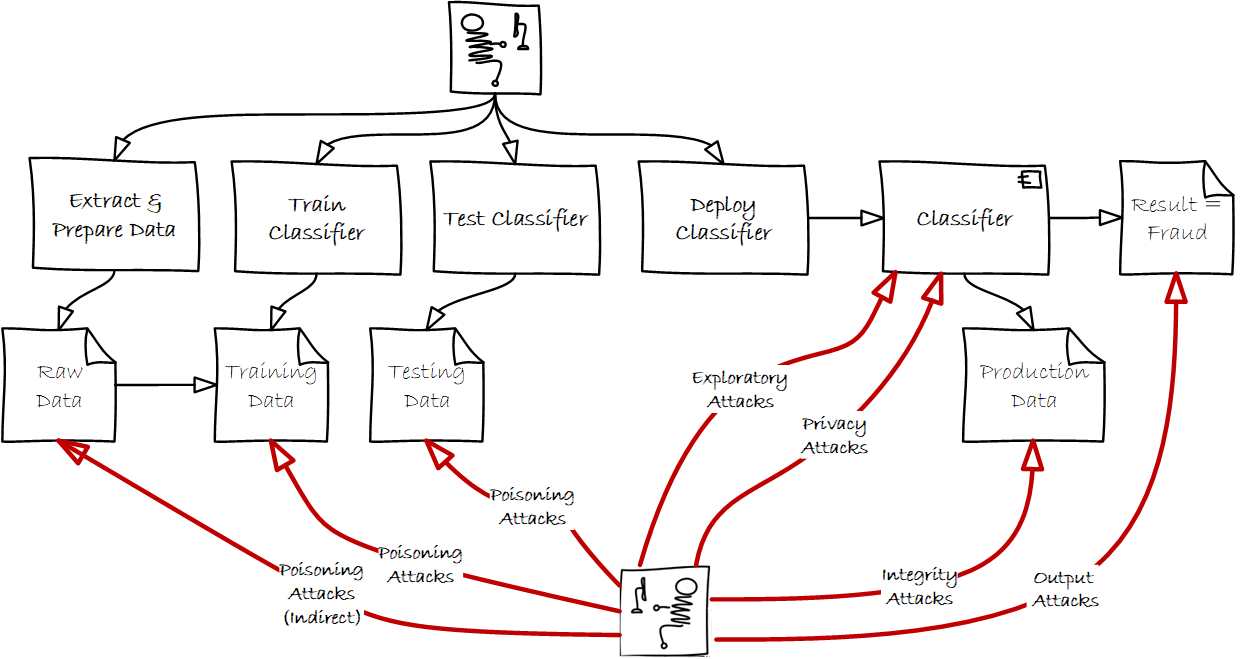
This is the second in a multi-part series that explores machine learning (ML) within cybersecurity. The first post in this…
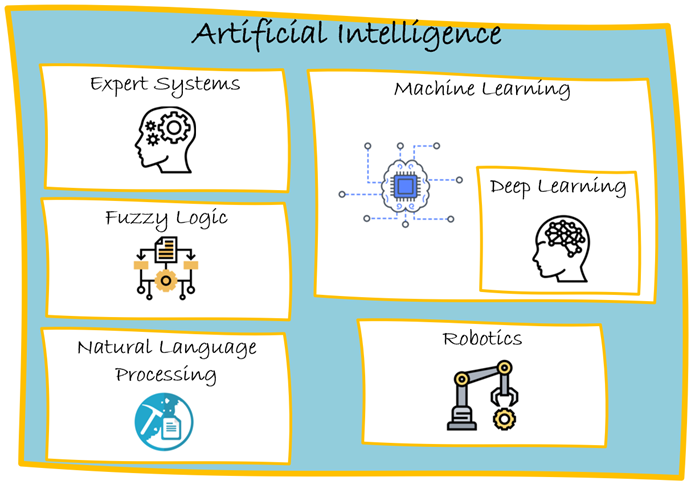
This post is the first in a multi-part series exploring machine learning (ML) within cybersecurity. When I first entered the…
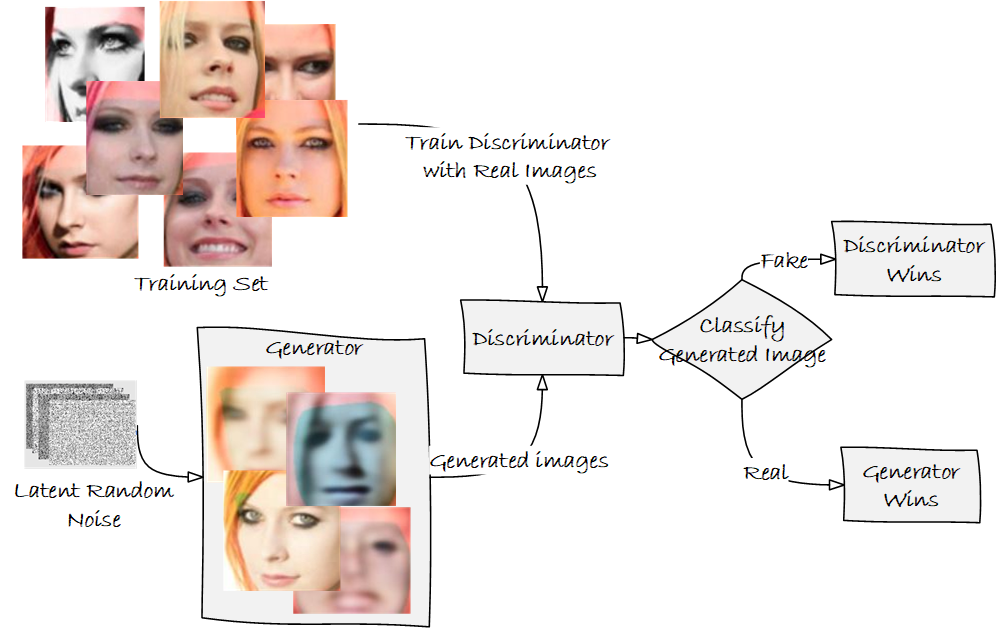
Imagine deepfake footage of a major, high-profile company CEO engaging in bribery, U.S. military personnel committing atrocities on foreign soil,…
Recently, I was asked my opinion regarding the most important role of a security engineer. This question made me think…
I will be presenting at the Borderless Cyber Conference in Washington, D.C. My presentation is scheduled for October 8th. I…
I recently had my first article published in a peer-reviewed journal. The Cyber Security & Information Systems Information Analysis Center…
As most of you know, I am a doctoral student at Colorado Technical University working on my dissertation. My research…
Organizations face a serious threat of data breaches caused by company insiders [1,2]. Traditional data loss prevention (DLP) tools and…
November 26, 2018, will mark the 10th anniversary of an incredible terrorist attack on Mumbai that shocked the world and…
Several years ago, when my son was in grade school, I was honored to represent the Marine Corps at a…
In previous posts, I have discussed the use of security automation and intelligence sharing to decrease the time to detect…
This week, I turn my attention to the concepts of denial and deception and their application to intelligence. Next week…
Next week, on 10/02 and 10/03, Johns Hopkins University Applied Physics Lab (JHU-APL) will be hosting the next Integrated Cyber…
This week, I change it up a little and take a break from discussing cybersecurity. Instead, I will discuss how…
The use of security automation and adaptive cyber defenses to combat cybercrime is an area of increasing research interest. Cyber…
Companies increasingly rely on information technology (IT) to remain competitive. Organizations invest heavily in technologies designed to protect valuable IT and…
Today, I will discuss how the failure to leverage strategic scenario planning led to the rapid decline of Wang Laboratories…