The use of security automation and adaptive cyber defenses to combat cybercrime is an area of increasing research interest. Cyber attackers enjoy a significant advantage over the defenders in cyber conflict [1,2]. The attackers’ advantage stems from multiple issues including the asymmetry of cyber conflict [1,2], the increased sophistication of cyber attacks [3,4], the speed and number of attacks [5], and a global shortage of cybersecurity talent [6,7,8,9]. Current human-centered cyber defense practices cannot keep pace with the threats targeting financial organizations [10].
Cyber defenders must address both sides of the equation to narrow the gap between the attackers’ time to compromise and the defenders’ time to respond. The leading research addresses the cyber defense disadvantage through community sharing of security intelligence, automation of security responses, and using innovative defenses including deception and active defense. An integrated approach involving security orchestration, automated response, information sharing, and advanced defense methods can reduce the competitive gap between attackers and defenders. Figure 1 depicts intelligence sharing, automated response, deception techniques, and advanced defensive methods working together to reduce the gap between the time to compromise and the time to respond.
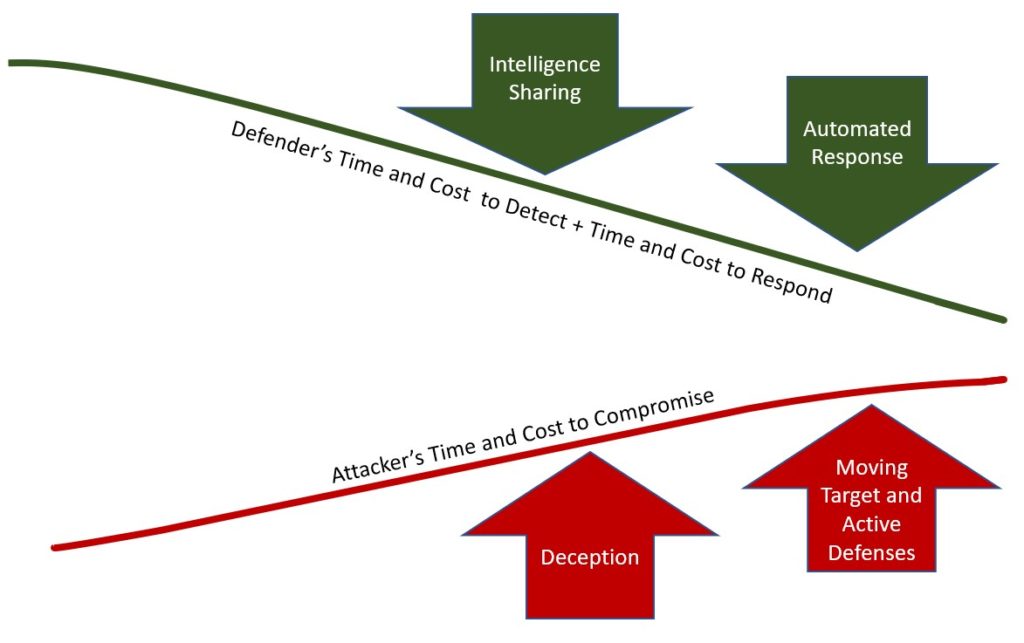
Intelligence sharing and automated response work together to reduce the defender’s cost and time. Information sharing can increase the efficiency in detecting and responding to cyber-attacks. Collaborating organizations can use the information shared by one organization to take preventative measures to thwart attacks [11]. Collective action, fostered by community sharing of intelligence can act as an immune system for the collaborating organizations. Security automation can increase the speed of response to an attack and the speed of proactively applying intelligence [10].
Cyber defenders can use many defensive methods to deter or delay attackers. Advanced defense methods, including moving target defenses, active defenses, and deception can raise the cost of an attack and slow the attack. Moving target defenses seek to increase the operational costs of the attackers by diversifying the attack surface presented to the attacker [2]. Active cyber defense countermeasures detect and mitigate threats in real-time and can take offensive actions both inside and outside of the defender’s network [12]. Deception can accomplish two major objectives. First, deception can slow the attacker and cause the attacker to expend resources [13]. Second, deception can reveal the attacker’s capabilities and techniques.
Researchers have shown that security automation and adaptive cyber defense techniques can enhance cybersecurity. The Integrated Adaptive Cyber Defense (IACD) framework, jointly developed by Johns Hopkins University Applied Physics Lab, the Department of Homeland Security, and the National Security Agency, provides a framework to close the gap between attacker and defender by leveraging automation, intelligence sharing, and advanced defensive capabilities [10]. More research is necessary to determine how organizations in the financial industry have employed or can employ security automation and adaptive cyber defense.
About the author: Donnie Wendt is an information security professional focused on designing and engineering security controls and monitoring solutions. Also, Donnie is an adjunct professor of cybersecurity at Utica College. Donnie is currently pursuing a Doctorate of Science in Computer Science with a research focus on security automation and orchestration.
References
[1] Carter, K. M., Okhravi, H., & Riordan, J. (2014). Quantitative analysis of active cyber defenses based on temporal platform diversity. OALib Journal. Retrieved from http://arxiv.org/abs/1401.8255v1
[2] Winterrose, M. L., Carter, K. M., Wagner, N., & Streilien, W. W. (2014). Adaptive attacker strategy development against moving target cyber defenses. ModSim World (pp. 1-11). Hampton, VA: ModSim World.
[3] Byrne, D. J. (2015). Cyber-attack methods, why they work on us, and what to do. AIAA SPACE 2015 Conference and Exposition (pp. 1-10). Pasadena, CA: American Institute of Aeronautics and Astronautics. doi:doi.org/10.2514/6.2015-4576
[4] Rivera, J., & Hare, F. (2014). The deployment of attribution agnostic cyberdefense constructs and internally based cyberthreat countermeasures. 6th International Conference on Cyber Conflict (pp. 99-116). Tallinn, Estonia: NATO CCD COE Publications. doi:10.1109/CYCON.2014.6916398
[5] Fonash, P., & Schneck, P. (2015, January). Cybersecurity: From months to milliseconds. Computer, 42-50. doi:10.1109/MC.2015.11
[6] Center for Strategic and International Studies. (2016). Hacking the skills shortage: A Study of the international shortage in cybersecurity skills. Santa Clara, CA: Intel Security. Retrieved from https://www.mcafee.com/us/resources/reports/rp-hacking-skills-shortage.pdf
[7] Cisco. (2015). Mitigating the cybersecurity skills shortage: Top insights and actions from Cisco Security Advisory Services. Cisco. Retrieved from https://www.cisco.com/c/dam/en/us/products/collateral/security/cybersecurity-talent.pdf
[8] Morgan, S. (2017). Cybersecurity Jobs Report: 2017 Edition. Herjavec Group. Retrieved from https://www.herjavecgroup.com/wp-content/uploads/2017/06/HG-and-CV-The-Cybersecurity-Jobs-Report-2017.pdf
[9] Suby, M., & Dickson, F. (2015). The 2015 (ISC)2 Global Information Security Workforce Study. Mountain View, CA: Frost & Sullivan. Retrieved from https://www.boozallen.com/content/dam/boozallen/documents/Viewpoints/2015/04/frostsullivan-ISC2-global-information-security-workforce-2015.pdf
[10] Johns Hopkins Applied Physics Laboratory. (2016). Integrated Adaptive Cyber Defense (IACD) Baseline Reference Architecture. Laurel, MD: Johns Hopkins Applied Physics Laboratory. Retrieved from https://secwww.jhuapl.edu/IACD/Resources/Architecture/IACD Baseline Reference Architecture – Final 0PR.pdf
[11] Zheng, D. E., & Lewis, J. A. (2015). Cyber Threat Information Sharing: Recommendations for Congress and the Administration. Washington, DC: Center for Strategic & International Studies. Retrieved from https://www.csis.org/analysis/cyber-threat-information-sharing
[12] Dewar, R. S. (2014). The triptych of cyber security: A classification of active cyber defense. 6th International Conference on Cyber Conflict (pp. 7-22). Tallinn, Estonia: NATO CCD COE Publications. doi:10.1109/CYCON.2014.6916392
[13] Raymond, D., Conti, G., Cross, T., & Nowatkowski, M. (2014). Key terrain in cyberspace: Seeking the higher ground. 6th International Conference on Cyber Conflict (pp. 287-300). Tallinn, Estonia: NATO CCD COE Publications. doi:10.1109/CYCON.2014.6916409