I have discussed the Integrated Adaptive Cyber Defense (IACD) from Johns Hopkins University Applied Physics Lab (JHU-APL) in previous posts. In this post, I will look at a concept underlying IACD and other response frameworks, the observe-orient-decide-act (OODA) loop. The OODA loop, developed by military strategist and Air Force pilot John Boyd, originally referred to gaining superiority in air combat. The concept behind the OODA loop was that completing an OODA loop quicker than the opponent prevented the opponent from gaining superiority in air combat. Organizations can also apply the OODA loop to cyber-incident response. If the defender can respond quickly to the attacker’s actions, before the attacker can complete the OODA loop, the defender can gain cyber superiority. According to JHU-APL (2016), the creators of the IACD framework, implementing the traditional OODA loop at speed and scale can decrease cyber-operation timelines from months to milliseconds [1].
Orientation is the Central Component of Boyd’s OODA loop
The OODA loop provides a framework for improving competitive advantage. However, the most common version of the OODA loop, which depicts the loop as a four-step linear process continuously operated in sequence, loses much of the power of Boyd’s original concept. Though Boyd often discussed the OODA loop, there is only one known sketch of the OODA loop by Boyd. Boyd’s sketch of the OODA loop, shown in Figure 1, appeared in a presentation from 1996. The OODA loop drawn by Boyd depicts the continuous interactions between the various steps, in which the steps are acting simultaneously.
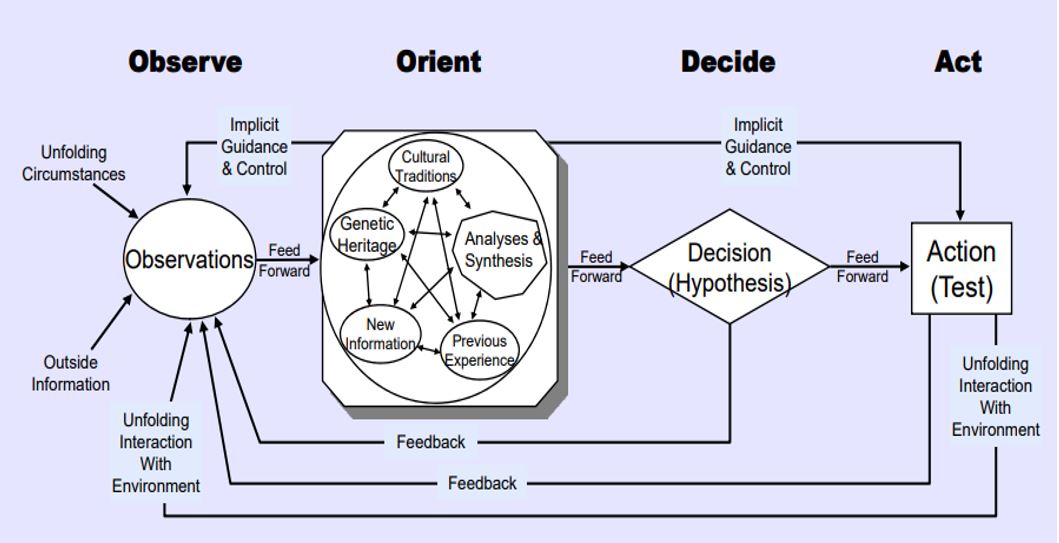
Boyd noted that orientation shapes observation, decision, and actions [2]. Feedback from the decisions and actions, along with observed phenomenon continually shape orientation. Thus, orientation plays the central role in Boyd’s OODA loop. Actions should flow from orientation implicitly, without explicit commands, most of the time. Boyd’s sketch shows implicit instructions flowing from orientation to guide both observation and action. Orientation embodies the concepts of mindfulness and situational awareness. According to Chet Richards, a close associate of Boyd, the emphasis on orientation and situational awareness turns conflicts into a contest to see which opponent can maintain awareness of the operational environment better [3]. Maintaining accurate situational awareness in a dynamic environment is critical to inform correct decisions and effective courses of action [4,5]. Each action taken further changes the situation requiring constant observation and orientation.
Operating in the Attacker’s OODA Loop
In Boyd’s seminal presentation on air combat in which Boyd developed the OODA loop concept, Boyd suggests that to win it is necessary to get inside the adversary’s OODA loop [6]. Interrupting the adversary’s OODA loop can cause confusion and disorder for the opponent. Changing the situation faster than the attacker can comprehend the changes can give the defender an advantage. Also, by inserting oneself into the opponent’s OODA loop, a combatant can discover the strengths, weaknesses, tactics, and intent of the adversary.
The underlying goal of the OODA loop is to be faster than the enemy [6]. This goal means that the cyber defender must streamline his command and control while also interfering with the attacker’s command and control. By generating a dominant tempo in the combat, the defender can disrupt the attacker’s ability to transition within the OODA loop. Deceiving humans and manipulating data streams within OODA loops can compromise the opponent’s decision-making activity. Operating in the attacker’s OODA loop using deceptions that disrupt the attacker’s orientation will compromise the attacker’s subsequent decisions and actions [7,8,9]. Deception-based defenses provide an advantage to the defenders as the deceptive information will affect the attacker’s observation and orientation stages of the OODA loop [8,9,10]. Defensive deceptions can help consume disrupt decision-making and consume the attacker’s resources by assigning additional tasks to the attacker [9,11,12]. Also, by slowing the attacker, the defender gains more time to further orient, decide, and act [8].
Zager and Zager use an example involving a phishing email attack to illustrate adding friction to an attacker’s OODA loop to disrupt decision-making [11]. Attackers often use bounce messages from email systems to guess email addresses of phishing targets. By understanding that the attacker’s OODA loop is using bounce messages to refine email address guesses, the defender can disrupt the attacker’s OODA loop. Defenders can apply friction to the attacker’s efforts by suppressing bounce messages and inserting random characters within employee email addresses. Further, since the attacker will have greater difficulty guessing email addresses, the logs will show an increase in the volume of rejected emails. This increased log data can provide additional forensic information for the security analysts.
Applying the OODA Loop to Cybersecurity
Researchers have proposed the application of the OODA loop to cybersecurity, especially to maintain situational awareness during a cyber-attack [1,13,14]. Jhwar et al. proposed a method to represent situational awareness during a cyber-attack using game theory [13]. Jhwar et al. support the concept that a holistic framework that includes achieving situational awareness, analysis of possible attacks, deciding upon the course of action, and acting is required to respond to cyberattacks [13]. The researchers apply the OODA loop to continually update the situational information about the state of the system and potential attacks and countermeasures. However, Jhwar et al. reduce the OODA loop to the common linear process in their research on cyber defense responses when they state that the OODA loop “…reverts to the Observe step after act.” [13] This simplification of the OODA loop deprives the OODA loop of the continuous, non-linear concepts proposed by Boyd.
Lenders et al. acknowledge the intricacies of the OODA loop and the continuous overlapping of the steps [14]. Observation and orientation occur simultaneously on different systems and on varying timescales. In addition to applying the OODA loop, Lenders et al. make a case for automation in their proposed framework to address situational awareness in the cyber realm [14]. According to the researchers, the complexity of technology, business, and information assets in large organizations demands automation tools to assist humans in gaining and maintaining situational awareness. Full awareness of the current situation within a complex cyber environment is impossible without automation.
Kallberg and Cook argue against the applicability of the traditional OODA-based command and control structure to the cyber realm [15]. According to Kallberg and Cook, four characteristics of the cyber realm undermine the applicability of the OODA loop: (a) the lack of permanence of objects; (b) the inability to effectively measure offensive cyber operations; (c) the speed of cyber operations does not allow for strategic leadership; and (4) the anonymity of the opponent. Kallberg and Cook focused on military operations, including offensive operations, in the cyber realm. Some of the arguments against the applicability of the OODA loop to defensive cyber operations do not apply. As discussed earlier, the actions taken within an OODA loop will mostly follow implicitly from orientation [2,3] devaluing the need for strategic leadership during the attack and response. Also, during the attack, the cyber defender is focused on stopping or mitigating the attack. The attacker’s anonymity may complicate defense but does not preclude the defender from taking defensive measures. However, anonymity can prevent possible retaliatory actions and make legal action more difficult [16].
Conclusion
Understanding the intricacies of the OODA loop can aid in defensive cyber operations. Cyber defenders must not view the OODA loop as a linear observe-then-orient-then-decide-then-act process. To properly apply the OODA loop to cyber operations, the combatant must understand the central role of orientation and the continuous interactions between the components of the OODA loop. Since the goal is to be quicker than the opponent, combatants should consider both sides of the equation. The use of automation and shared intelligence can help reduce the time to detect and respond. The application of defensive tactics such as deception and moving target defenses can slow the attack. By addressing both sides of the equation and operating within the adversary’s OODA loop, defenders can begin reducing the attackers’ asymmetric advantages.
References
[1] Johns Hopkins Applied Physics Laboratory. (2016). Integrated Adaptive Cyber Defense (IACD) Baseline Reference Architecture. Laurel, MD: Johns Hopkins Applied Physics Laboratory. Retrieved from https://secwww.jhuapl.edu/IACD/Resources/Architecture/IACD Baseline Reference Architecture – Final 0PR.pdf
[2] Boyd, J. R. (1996). The essence of winning and losing. (C. Spinney, C. Richards, & G. Richards, Eds.) Retrieved from http://dnipogo.org/john-r-boyd/
[3] Richards, C. (2011). Boyd’s OODA loop (it’s not what you think). Proceedings of the Lean Software & Systems Conference 2011 (pp. 127-136). Sequim, WA: Blue Hole Press.
[4] Pahi, T., Leitner, M., & Skopik, F. (2017). Analysis and assessment of situational awareness models for national cyber security centers. International Conference on Information Systems Security and Privacy. Porto, Portugal. Retrieved from http://www.flosko.at/ait/2017_icissp.pdf
[5] Dressler, J., Moody, W., Bowen, I. C., & Koepke, J. (2014). Operational data classes for establishing situational awareness in cyberspace. 6th International Conference on Cyber Conflict (pp. 175-186). Tallinn, Estonia: NATO CCD COE Publications. doi:10.1109/CYCON.2014.6916402
[6] Boyd, J. R. (1986). Patterns of conflict. Retrieved from http://dnipogo.org/john-r-boyd/
[7] Zager, R., & Zager, J. (2016, September). Why we will continue to lose the cyber war: A response to cyber proficient force 2015 & beyond. Small Wars Journal. Retrieved from https://www.researchgate.net/profile/Robert_Zager/publication/308352725_Why_We_Will_Continue_to_Lose_the_Cyber_War/links/57e1acfb08aed96fbbb07594.pdf
[8] Almeshekah, M. H., & Spafford, E. H. (2016). Cyber Security Deception. In S. Jajodia, V. Subrahmanian, V. Swarup, & C. Wang (Eds.), Cyber Deception (pp. 23-50). Switzerland: Springer. doi:10.1007/978-3-319-32699-3_2
[9] Stech, F. J., Heckman, K. E., & Strom, B. E. (2016). Integrating cyber-D&D into adversary modeling for active cyber defense. In S. Jajodia, V. S. Subrahmanian, V. Swarup, & C. Wang (Eds.), Cyber Deception (pp. 1-22). Switzerland: Springer. doi:10.1007/978-3-319-32699-3_1
[10] Virvilis, N., Serrano, O. S., & Vanautgaerden, B. (2014). Changing the game: The art of deceiving sophisticated attackers. 6th International Conference on Cyber Conflict (pp. 87-97). Tallinn, Estonia: NATO CCD COE Publications. doi:10.1109/CYCON.2014.6916397
[11] Zager, R., & Zager, J. (2017, October). OODA loops in cyberspace: A new cyber-defense model. Small Wars Journal. Retrieved from https://www.researchgate.net/profile/Robert_Zager/publication/320809843_OODA_Loops_in_Cyberspace_A_New_Cyber-Defense_Model/links/59fb88dd0f7e9b9968ba6bd7/OODA-Loops-in-Cyberspace-A-New-Cyber-Defense-Model.pdf
[12] Raymond, D., Conti, G., Cross, T., & Nowatkowski, M. (2014). Key terrain in cyberspace: Seeking the higher ground. 6th International Conference on Cyber Conflict (pp. 287-300). Tallinn, Estonia: NATO CCD COE Publications. doi:10.1109/CYCON.2014.6916409
[13] Jhwar, R., Mauw, S., & Zakiuddin, I. (2016). Automating cyber defence responses using attack-defence trees and game theory. The 15th European Conference of Cyber Warfare and Security (pp. 163-172). Munich, Germany: Academic Conferences and Publishing International.
[14] Lenders, V., Tanner, A., & Blarer, A. (2015). Gaining an edge in cyberspace with advanced situational awareness. IEEE Security & Privacy, 13(2), 65-74. doi:10.1109/MSP.2015.30
[15] Kallberg, J., & Cook, T. S. (2017). The unfitness of traditional military thinking in cyber: Four cyber tenets that undermine conventional strategies. IEEE Access, 5, 8126-8130. doi:10.1109/ACCESS.2017.2693260
[16] Dewar, R. S. (2014). The triptych of cyber security: A classification of active cyber defense. 6th International Conference on Cyber Conflict (pp. 7-22). Tallinn, Estonia: NATO CCD COE Publications. doi:10.1109/CYCON.2014.6916392